We continue our series of articles focused on testing systems that incorporate Multi-Factor Authentication (MFA or 2FA) security mechanisms. In our previous article about MFA testing, we explored why companies operating in regulated industries must adopt these mechanisms to strengthen their security.
Although there is a wide range of MFA solutions available, most companies favor those that provide a smooth and simple user experience, such as MFA via SMS, email, or TOTP.
In this article, we will delve into a crucial topic: what are the challenges related to testing workflows that include MFA, and what strategies can be adopted to overcome them?

1. Key Challenges in MFA Test Automation
1.1 Dependency on External Devices
By design, MFA relies on external devices, such as phones for receiving SMS or apps for generating TOTP codes. This reliance complicates test automation, especially when multiple accounts are involved:
- Email MFA: QA teams commonly use alias-based email structures (e.g., user+alias@domain.com) to streamline account creation. However, these methods might be limited or disabled in corporate settings, complicating automation efforts. On top of that, retrieving emails from third-party providers is a challenge.
- SMS MFA: Each user account typically requires a unique phone number. This leads to logistical issues, such as managing physical SIM cards or sharing test phones, which undermines efficiency and scalability. Ever had to call your colleague so they can share the MFA code retrieved on their phone?
- TOTP MFA: Time-based One-Time Passwords require secure handling of private keys. Automating tests becomes intricate, as these keys are usually inaccessible after initialization.
1.2 Limited Automation Feasibility
MFA workflows interact with external systems, making them hard to automate and often impractical, particularly for third-party services like email providers (e.g., Outlook). Automating such interactions is resource-intensive and often restricted by service providers that block bot connections.
1.3 Risky Approach #1: Disabling MFA in Test Environments
To save time, some teams disable MFA in testing environments. While expedient, this approach introduces significant risks:
- Increased Security Risk:
- Accounts become less secure in testing environments, as MFA becomes optional.
- Divergent behavior from the production environment undermines test validity, as you might discover issues in production caused by a misconfiguration.
- Less Representative Tests: Tests fail to reflect real-world production conditions, increasing the likelihood of undetected bugs surfacing in production.
- Human Errors: Configuration differences between testing and production environments complicate deployments, sometimes resulting in accidental policy misconfigurations in production.
- Incomplete Tests: Key steps like login processes or transaction validation are skipped, reducing the ability to detect issues in critical functionalities.
1.4 Risky Approach #2: Intercepting MFA in Testing Environments
While better than disabling MFA, this approach still risks configuration divergence between environments and potential errors during deployment (i.e. discovering issues in production).
1.5 A costly but Effective Approach: Interfacing with Third-Party Providers
This method, although sometimes costly and complex, can be highly beneficial if your service providers (email or SMS) offer APIs or interfaces compatible with automation tools like Cypress or Robot Framework. Tools like Eggplant can also help achieve this goal.
These integrations allow you to directly extract MFA codes and incorporate them into your automated test scripts.
However, it is often necessary to proactively communicate with these providers, as they may be reluctant to allow automated access to their systems. For instance, you might find it is quite hard to automate outlook login and email content retrieval through a web interface. Despite these challenges, this approach ensures realistic testing aligned with production scenarios.
2. Strategies for Automating and Testing End-to-End MFA Workflows
2.1 Align Testing Environments with Production
Ensuring parity between testing and production environments is essential for identifying potential issues effectively. Leveraging tools to retrieve MFA codes via email, SMS, or APIs can offer the following benefits:
- Improved UX/UI Detection: Reproducing production conditions helps identify anomalies in the user experience or interface.
- Load Management: Testing under production-like constraints uncovers system weaknesses, such as throttling issues or usage limits for MFA services.
- Third-Party Service Validation: Verifies proper integrations and ensures messages aren not lost. Load testing can also reveal vulnerabilities under heavy usage.
2.2 Collaborative Manual Testing Solutions
For manual testing, collaborative solutions can simplify MFA management within QA teams:
- Email: Use shared mailboxes with aliases (e.g., testing+xyz@company.io) to centralize code reception. If your IT department does not allow you to use such features, you might need to consider an alternative approach from a third party. For instance, virtual mailbox services like GetMyMFA offer private email addresses to retrieve MFA codes.
- SMS: Solutions like GetMyMFA offer private virtual phone numbers, avoiding physical devices. Free options like Receive-SMS-Free exist but pose risks due to publicly shared numbers. This represents an issue as your organization’s SMS messages can become public (Search Engine indexing).
- TOTP: Securely share secret keys using password managers like Bitwarden or 1Password. This enables teams to access temporary codes without physical devices while managing key access effectively.
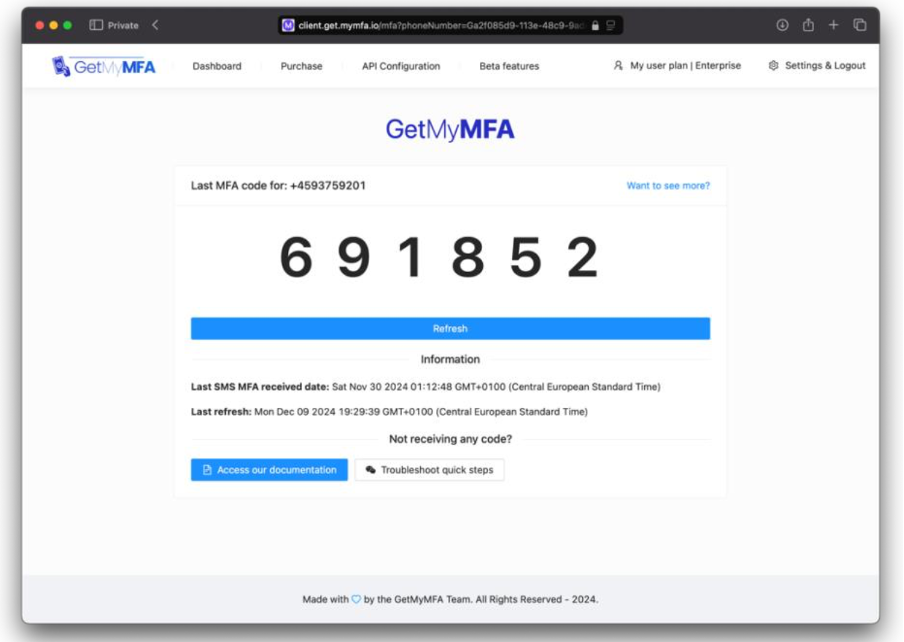
2.3 Automation Tools for MFA Testing
Automating MFA tests requires tools that simplify interactions with authentication mechanisms. Specialized APIs streamline this process, reducing the need for complex manual integrations and fighting providers on bot-blocking policies. Examples include:
- Email APIs: Services like MailSlurp or GetMyMFA allow generating temporary email addresses to automate code retrieval via APIs.
MFA retrieval illustration through GetMyMFA’s programmatic API
-
- SMS APIs: Virtual phone number providers, such as GetMyMFA, simplify automating SMS MFA workflows by exposing a public and secure API which extracts the MFA codes received to your private phone numbers. This allows to avoid purchasing and handling SIM cards. On top of that, you can easily share the phone numbers with the QA team members.

- TOTP APIs: Providers offer solutions for importing private TOTP keys, exposing OTP codes via APIs.
Conclusion
Effectively testing workflows that incorporate Multi-Factor Authentication (MFA) mechanisms remains a challenge for QA teams, who often end up disabling MFA in staging environments. However, it is essential to test these flows to ensure the reliability and security of systems in production. The constraints related to automation and manual testing (particularly the handling of external devices and interactions with third-party services) highlight that a simplistic or rushed approach can lead to significant risks, whether in terms of security, test validity, or tester experience.
Using specialized tools-such as email inbox management services or virtual phone number platforms-alongside collaborative strategies for manual testing allows teams to simulate production-like conditions as closely as possible. These approaches not only minimize the gap between testing and production environments, but also enhance the team’s ability to detect critical issues before deployment.
In conclusion, adopting a well-thought-out strategy for MFA testing-combining the right tools, collaborative processes, and automation best practices-is essential to meet this challenge. It ensures that MFA workflows perform as expected in a precise and repeatable manner.
Not only does this strengthen the robustness of MFA flows, but it also protects end users and improves anomaly detection. With such an approach, companies can ensure their systems are both secure and reliable, while still delivering a high-quality user experience.
About the Author: Jonathan Bernales
I am the CTO at Germen, an InsurTech company building tech platforms for both corporate and individual clients. I am passionate about building and using technology that allows teams to deliver high-quality code in complex environments without compromising on security or speed. I am also the founder of GetMyMFA.

