We continue our series of articles dedicated to testing systems that integrate Multi-Factor Authentication (MFA or 2FA) security mechanisms!
In our first article, we explored how Multi-Factor Authentication (MFA) has become an essential standard for securing online applications and services. Its widespread adoption helps strengthen user account protection against cyberattacks. Increasingly, companies are focusing on implementing these measures, which are becoming mandatory, particularly within the financial sector.
However, within enterprises, integrating MFA presents a significant challenge for automated testing. MFA workflows should not simply be disabled in test and UAT environments, as doing so could compromise the reliability of functional validations by creating a scenario that deviates from production conditions (potentially leading to the late discovery of previously untested issues). Therefore, tests must include Multi-Factor Authentication to ensure an experience as close as possible to the real production environment.
In the second article, we discussed various strategies for automating these MFA tests. We also introduced tools such as GetMyMFA, MailSlurp, and Receive-SMS-Free.cc, which facilitate automation for receiving and processing MFA codes.
In this third article, we will examine how test teams can effectively collaborate in these complex scenarios and how automation through Robotic Process Automation (RPA) can simplify processes that have traditionally been handled manually in production.
1. Using webhooks for collaborative working
Automating MFA tests does not eliminate the need to perform manual tests. These tests often involve teams working together on shared accounts, especially when handling codes sent via email, SMS, or TOTP applications. Accessing these codes collaboratively can become complex, as each user must be able to obtain the MFA code without conflicts or excessive delays. Poor organization can quickly hinder both productivity and test security. This is where webhooks offer an effective solution by automating the transmission of MFA codes to a shared communication channel, enabling all team members to collaboratively access real-time information.
1.1 Approach with third-party services
1.1. MFA codes sent via email:
If you have the possibility to request this from your IT department, an effective approach is to create a Google Group (if you’re using Google Workspace) or a shared mailbox (Shared Mailbox, if you’re using Microsoft 365). These systems allow multiple users to simultaneously access emails containing MFA codes without needing to forward them individually. Additionally, this works seamlessly with the mechanism known as “Plus addressing” enabling you to create as many “sub-accounts” as needed (e.g., test+user1@domain.com, test+user2, etc.).
Illustration of a shared GoogleGroup team
1.1.2 SMS-based MFA codes:
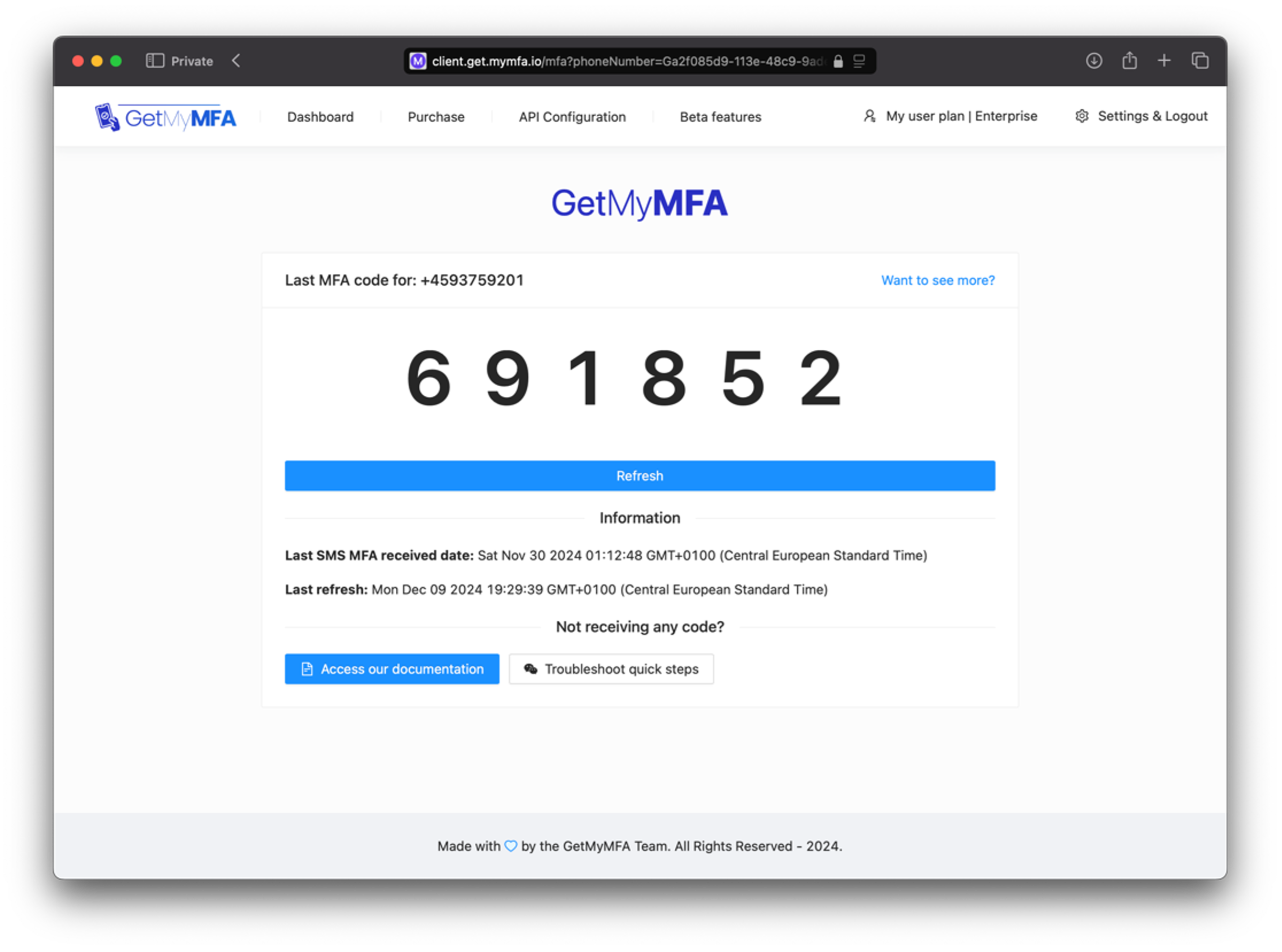
Let us avoid sharing phones loaded with multiple SIM cards! While this might provide a quick fix in the short term, it’s neither practical nor sustainable. A better alternative is using private or shared virtual phone numbers provided by services such as GetMyMFA (paid) or Receive-SMS-Free.cc (free). These services allow easy access to MFA SMS codes through a web interface or an API, streamlining the automation process and simplifying code-sharing among testers. They also ensure that your setup is consistent with your production environment:
GetMyMFA interface showing phone number MFA sharing
1.1.3 For temporary (TOTP) codes:
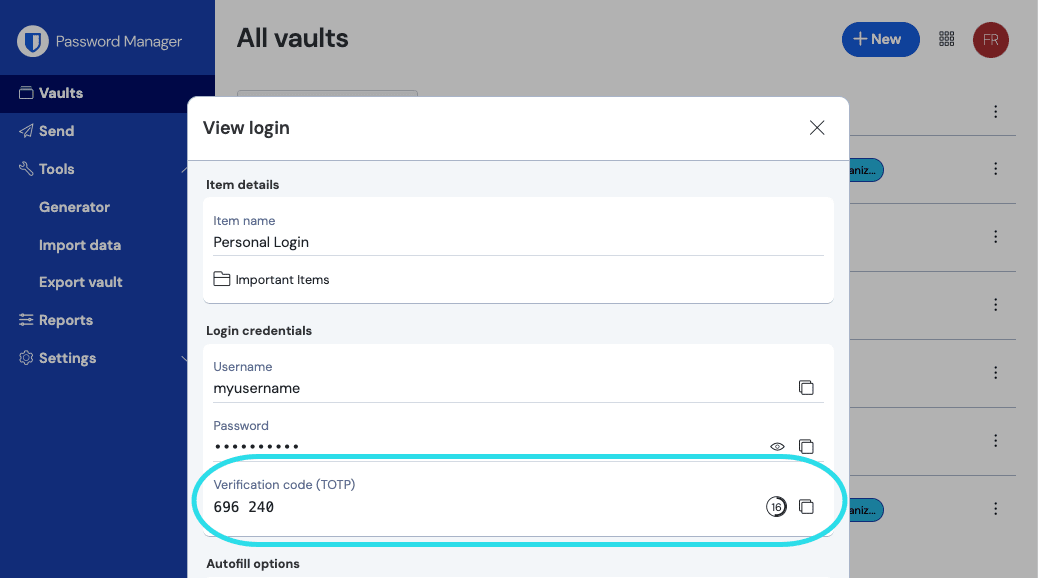
The best approach is to use secure password managers such as Bitwarden or 1Password. These tools allow you to securely store and share TOTP secret keys, ensuring that each team member can generate the required MFA codes without compromising data privacy.
By combining these various tools and methods, you can perform numerous MFA tests while maintaining a high level of security and collaboration. The goal is to ensure seamless, frictionless access to MFA codes, aligned closely with your testing needs.
Bitwarden’s interface to access and share TOTP codes
1.2 Using webhooks to simplify and improve team collaboration
1.2.1 What is a webhook
A webhook is a mechanism that sends real-time notifications from one system to another using an HTTP request. Unlike traditional APIs, which require actively polling a system to retrieve data, webhooks automatically push information the moment an event occurs.
In the context of MFA testing, webhooks are particularly useful for automating authentication codes sharing among team members. They allow codes to be instantly delivered to collaborative tools such as Microsoft Teams, Slack, or Google Workspace, eliminating waiting times and manual interventions. Thus, there is no longer a need to check APIs or websites manually to retrieve your MFA codes: they automatically arrive in your preferred collaboration tools.
1.2.2 How to use webhooks collaboratively
The use of webhooks for MFA testing depends on integrating them with authentication code management services. Providers such as MailSlurp, Mailosaur, or GetMyMFA offer these features. With these services, you can set up a webhook that automatically retrieves MFA codes from emails or SMS messages and forwards them directly into your chosen communication channel, such as Slack, Microsoft Teams, or Google Workspace.
If you prefer a DIY approach, you could also build a custom solution, for example using the Google API along with a watcher. However, this approach is heavier and more complex to set up.
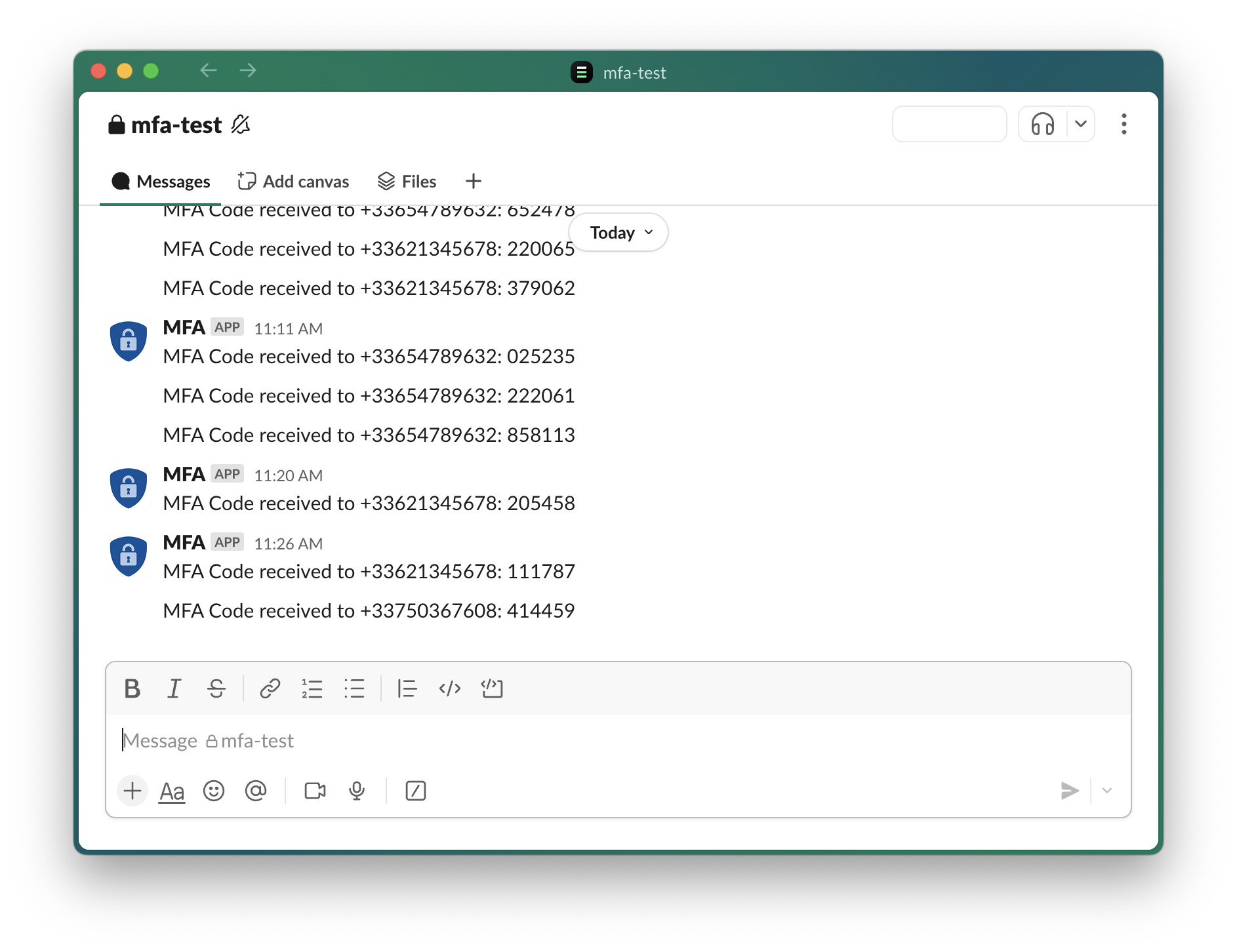
Taking GetMyMFA as an example (though the process is similar for other services), configuring a webhook starts by saving a receiving URL generated by your messaging platform. Platforms like Slack or Teams provide straightforward instructions on how to do this. Each time an MFA code is generated, it’s immediately and automatically shared with all team members in real-time. Below is an example illustrating the result within a shared Slack or Teams channel:
Slack channel example retrieving MFA codes from a webhook
Teams group example showing MFA codes being shared with the team
By centralizing all MFA codes in a single location, we ensure seamless and immediate code delivery, allowing you and your team to focus on executing tests without interruptions. Moreover, this approach enhances transparency and traceability by maintaining a history of shared codes directly within your corporate communication tools.
1.3 In essence
The third-party services-based approach-whether for emails, SMS, or TOTP codes-enables centralization and easier access to authentication data. For instance, using shared mailboxes or Google Groups allows QA teams to efficiently review MFA-related emails without risking information loss or duplication. Similarly, adopting third-party services offers an effective solution for managing MFA codes received via SMS, eliminating issues associated with physically sharing mobile devices. Lastly, shared password managers such as Bitwarden and 1Password simplify secure access to TOTP codes.
On the other hand, webhooks represent an ideal solution for automating and streamlining real-time sharing of MFA codes. Their main advantage is that they require no modifications to the source systems and do not disrupt existing infrastructure. Additionally, integrating webhooks with collaboration platforms like Slack, Microsoft Teams, or Google Workspace help companies achieve effective collaboration among testers.
2. Introduction to RPA
Although not directly within the scope of testing, Robotic Process Automation (RPA) is a practice that can greatly benefit from enhanced security mechanisms.
2.1 What is “RPA”?
RPA is a technology that automates IT processes by simulating human actions on software interfaces. It relies on software “robots” capable of performing structured and repetitive tasks without human intervention. In practical terms, RPA involves deploying a “bot” that mimics a human user to execute tasks that are easily automatable on third-party services-for example, validating supporting documents when a user submits bank details. Since “acting like a human” also means “authenticating as a human,” it inherently brings associated security risks.
2.2 Why do businesses do RPA?
Businesses adopt RPA to achieve several strategic objectives. First, this technology reduces human error by standardizing procedures and eliminating manual interventions prone to mistakes. Then, RPA significantly saves time by quickly and efficiently handling repetitive tasks, enabling teams to focus on activities with higher added value.
A key example is the validation process for supporting documents. By combining RPA with Optical Character Recognition (OCR), companies can deploy a robot capable of validating customer submissions and transitioning their processing status across multiple third-party production systems (such as Salesforce, JIRA, etc.).
2.3 Mitigeons les risques liés au RPA
While RPA provides significant advantages, it is crucial to ensure its use does not compromise system security. Access management for these robots must be rigorously controlled to prevent credential compromise or malicious usage.
Several best practices include:
- Implementing corporate Single Sign-On (SSO) so robots authenticate using the same processes as regular employees.
- Regular rotation of robot passwords.
- Enforcing MFA authentication: Allowing robots to have multi-factor authentication ensures they maintain the same security standards as other production users. Services like GetMyMFA can provide MFA codes automatically via API integration into RPA processes.
By implementing these security measures, companies can fully leverage RPA’s potential while maintaining a high security posture. Integrating RPA with MFA testing thus optimizes processes and ensures a secure, seamless user experience.
Conclusion and summary
We developed this series of three articles to address fundamental concepts related to implementing multi-factor security and its impact on testing processes. Here is a brief summary:
- Article 1:
- MFA is becoming standard across business applications. Multiple methods exist, including sending codes via email, SMS, physical keys, or generating temporary codes using unique tokens. Although email and SMS MFA aren’t the most secure methods, businesses commonly prefer them due to their ease of use for end-users.
- Article 2:
- Securing MFA workflows poses challenges during automated testing-which makes sense since one of MFA’s purposes is to reinforce authentication robustness. Consequently, QA teams may be tempted to disable MFA in testing environments. This practice is problematic because significant performance or operational issues may only emerge in production (i.e. too late). Paradoxically, MFA-protected workflows are usually the most critical and therefore need extensive testing despite their complexity.
- Solutions that facilitate receiving and sharing MFA codes via email and SMS, such as GetMyMFA or Mailosaur, offer a practical compromise: enabling secure testing in an environment closely mirroring production. This leads to enhanced cybersecurity posture, improved test coverage, and greater relevance of test scenarios.
- These solutions also provide APIs that allow MFA flows to be received and processed programmatically by automation tools like Postman, Playwright, or Cypress, among others.
- Article 3:
- On top to all the above, it is possible to leverage these solutions to create a centralized environment for code sharing among teams by using webhooks connected to common messaging platforms such as Teams, Slack, or Google Workspace.
- These tools also enable organizations to secure their RPA workflows by ensuring multi-factor protected authentication.
We hope you enjoyed this article series and found valuable insights! If you have any further questions or would like to discuss these topics in more detail, please feel free to reach out. We’re always happy to help! :)
About the Author: Jonathan Bernales
I am the CTO at Germen, an InsurTech company building tech platforms for both corporate and individual clients. I am passionate about building and using technology that allows teams to deliver high-quality code in complex environments without compromising on security or speed. I am also the founder of GetMyMFA.