Knowledge and tools for security testing and all the security aspects of software testing.
Connectivity today reaches far beyond desktops and smartphones. The Internet of Things (IoT) now powers smart homes, industrial automation, automotive systems, medical devices, and nationwide infrastructure. Yet this expanded digital footprint also widens the attack surface-which in the context of IoT means cyberattacks can escalate into physical consequences.
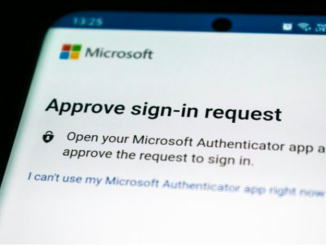
We continue our series of articles dedicated to testing systems that integrate Multi-Factor Authentication (MFA or 2FA) security mechanisms!
Cyberattacks are becoming more advanced and are occurring more often, with the cost of cybercrime expected to reach $15.63 trillion by 2029. Older security methods just can’t keep up with evolving threats, which is where Artificial Intelligence (AI) and Machine Learning (ML) come in.
We continue our series of articles focused on testing systems that incorporate Multi-Factor Authentication (MFA or 2FA) security mechanisms. In our previous article about MFA testing, we explored why companies operating in regulated industries must adopt these mechanisms to strengthen their security.
Welcome to this series of three articles dedicated to an in-depth analysis of testing systems that integrate multi-factor authentication (MFA) mechanisms. If you work in a regulated entity, particularly in the financial or banking sectors, you have likely faced the challenges associated with testing MFA-protected workflows such as authentication and financial transactions.
What does it mean to safeguard your app? It simply means preventing an infiltration by hackers. However, that’s only part of the definition. You also need to make sure that only the right people get access to the right data. Imagine if someone unauthorized were to gain access to your app – They could get all the sensitive user data and confidential information.
The Cryptography market is growing every day and therefore, the need for enhanced security in crypto applications has never been felt before. When using crypto applications, it is important to ensure their security due to the current increase in cyber threats.